2023-06-01-某点资讯Signature纯算逆向

某点资讯Signature纯算逆向
本篇主要是介绍一些工作的运用熟练性,以及跟踪堆栈去看是否做一些其他操作等:
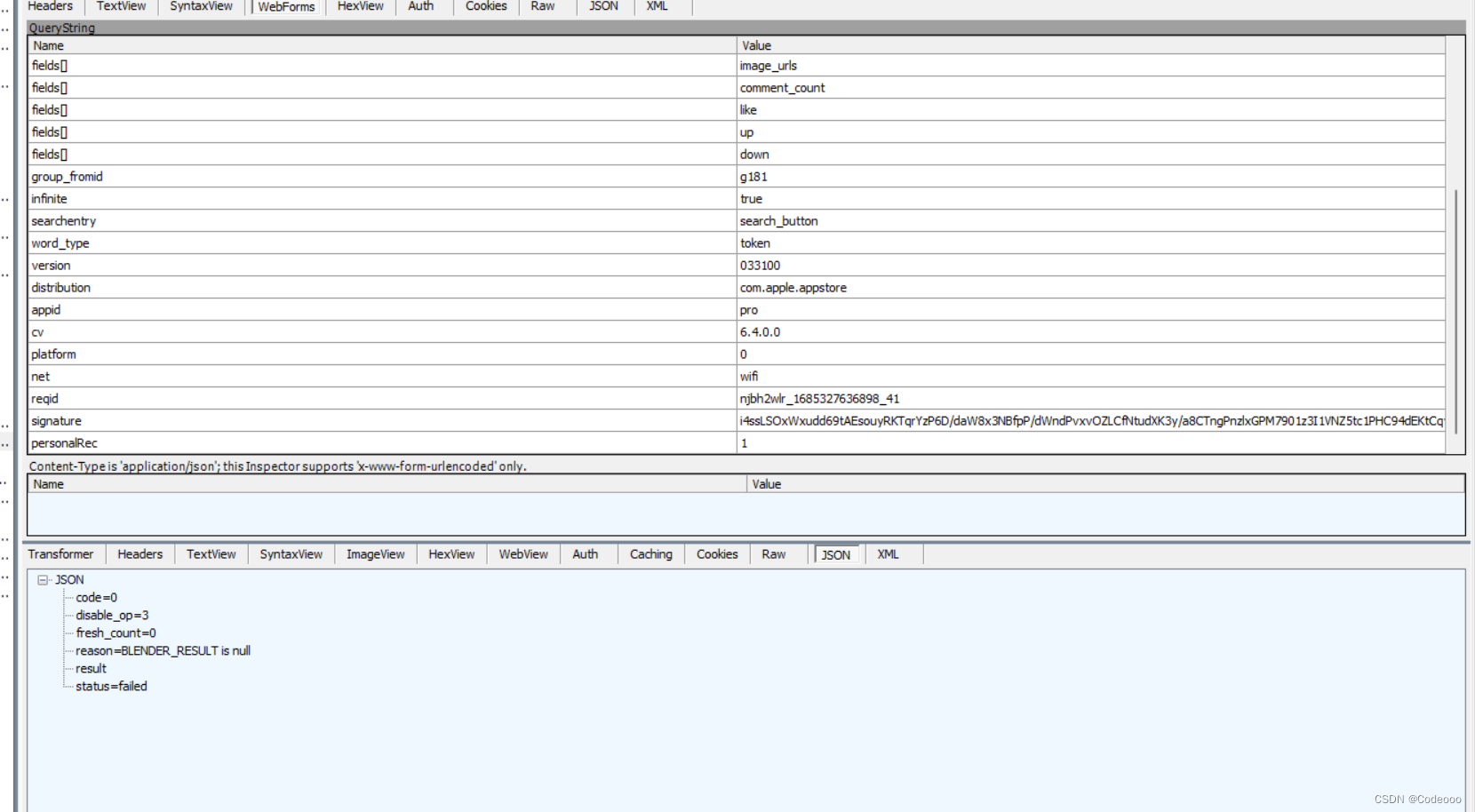
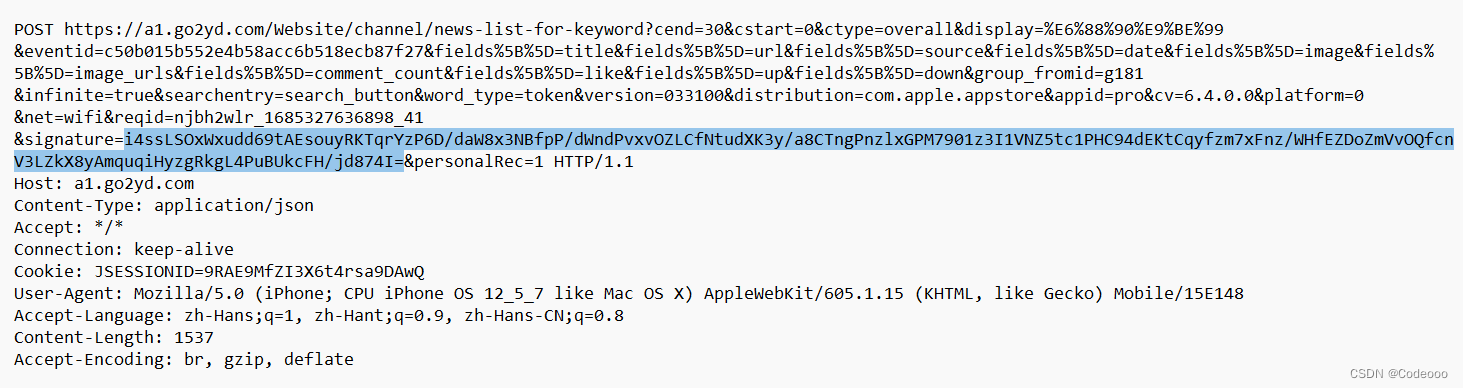
抓包:
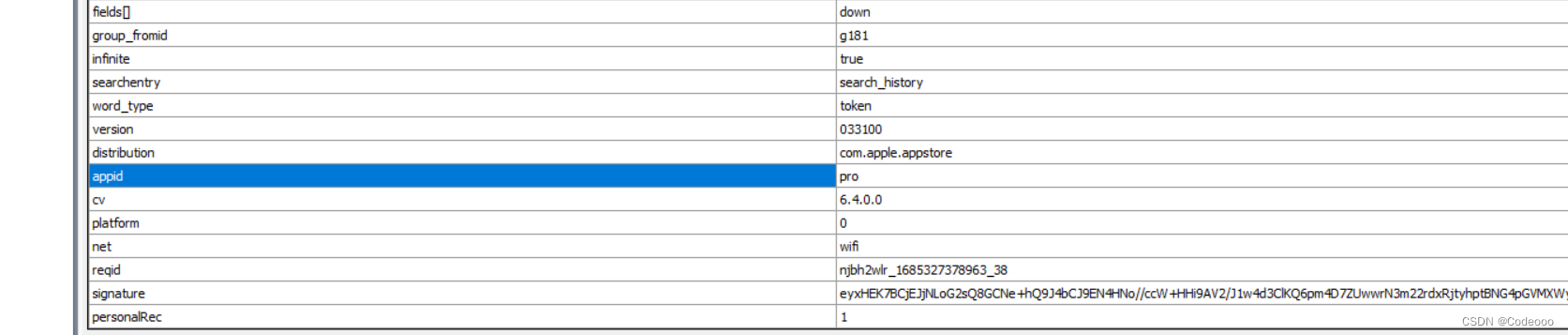
signature 为加密值;
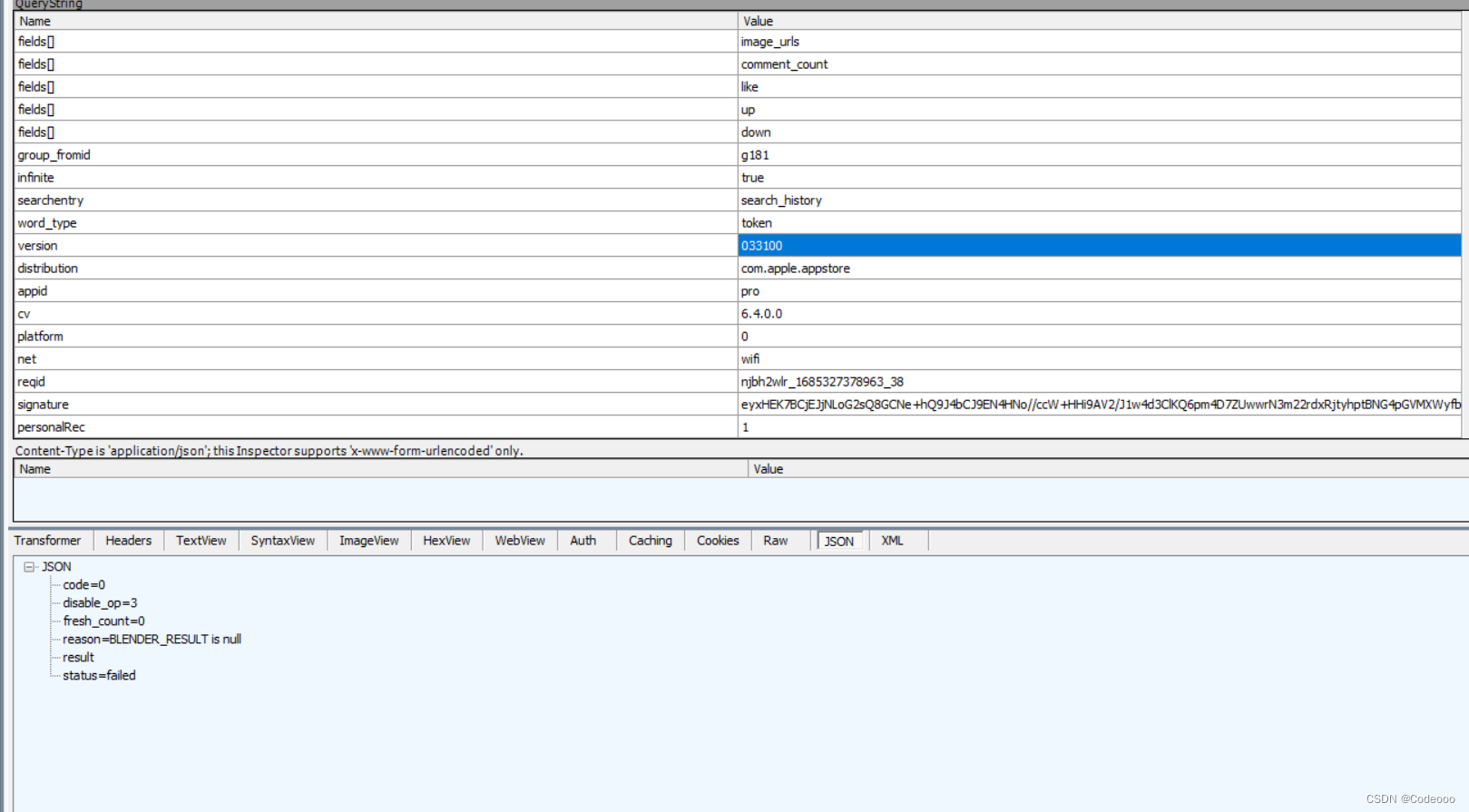
先上trace下堆栈及加密
我们把结果base64下,看结果是否一致,来判断base64是否魔改
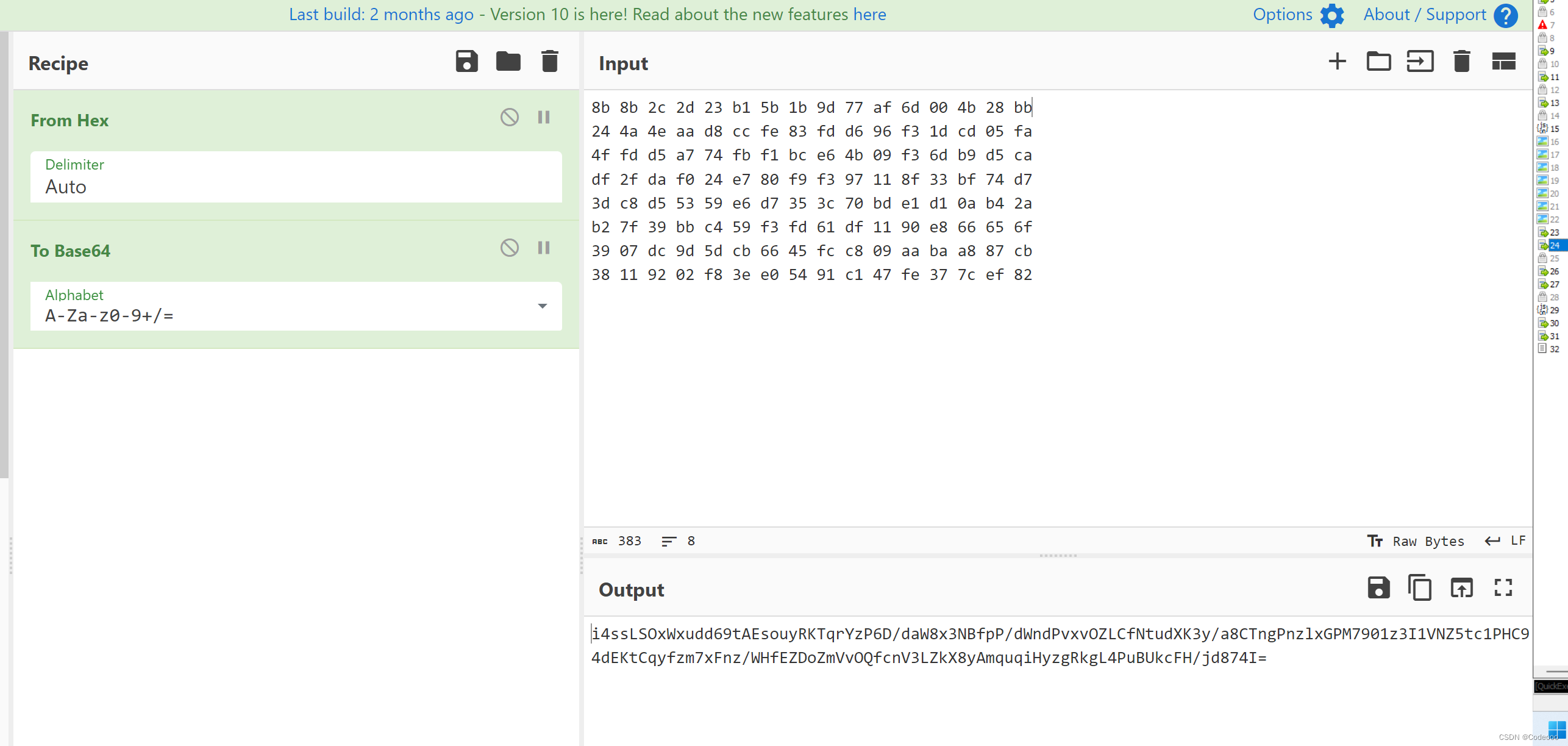
验证base64为标准;
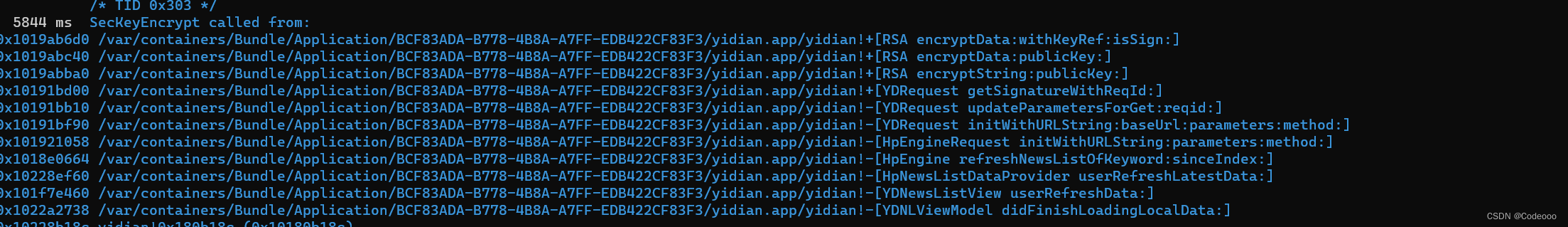
根据刚刚的堆栈,跟一下
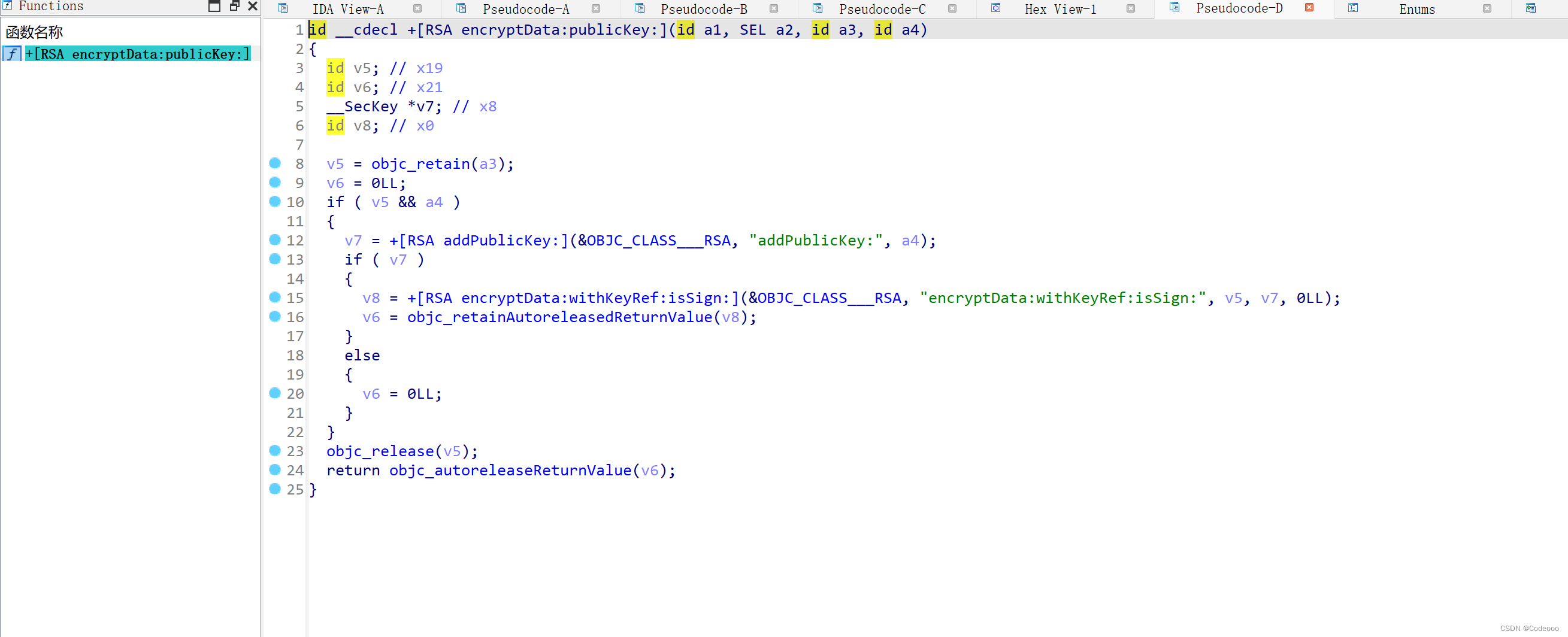
0x101115468 /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!+[RSA encryptData:withKeyRef:isSign:]
0x101115ae0 /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!+[RSA encryptData:publicKey:]
0x101115a28 /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!+[RSA encryptString:publicKey:]
0x10108a8ac /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!-[YDRequest getSignatureWithReqId:]
0x10108a6b0 /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!-[YDRequest updateParametersForGet:reqid:]
0x10108aaf4 /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!-[YDRequest initWithURLString:parameters:method:]
0x10108e300 /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!-[HpEngineRequest initWithURLString:parameters:method:]
0x101047544 /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!-[HpEngine refreshNewsListOfKeyword:sinceIndex:]
0x101a17858 /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!-[HpNewsListDataProvider userRefreshLatestData:]
0x1017be2ac /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!-[YDNewsListView userRefreshData:]
0x101a235bc /var/containers/Bundle/Application/9580891A-98B0-4F3F-9938-D794221B5B4D/yidian.app/yidian!-[YDNLViewModel didFinishLoadingLocalData:]
0x101a166f0 yidian!0x16ae6f0 (0x1016ae6f0)
0x232360a38 libdispatch.dylib!_dispatch_call_block_and_release
0x2323617d4 libdispatch.dylib!_dispatch_client_callout
0x23230f008 libdispatch.dylib!_dispatch_main_queue_callback_4CF
V A R I A N T VARIANT
V
A
R
I
A
NT mp
0x2328b4b20 CoreFoundation! CFRUNLOOP_IS_SERVICING_THE_MAIN_DISPATCH_QUEUE
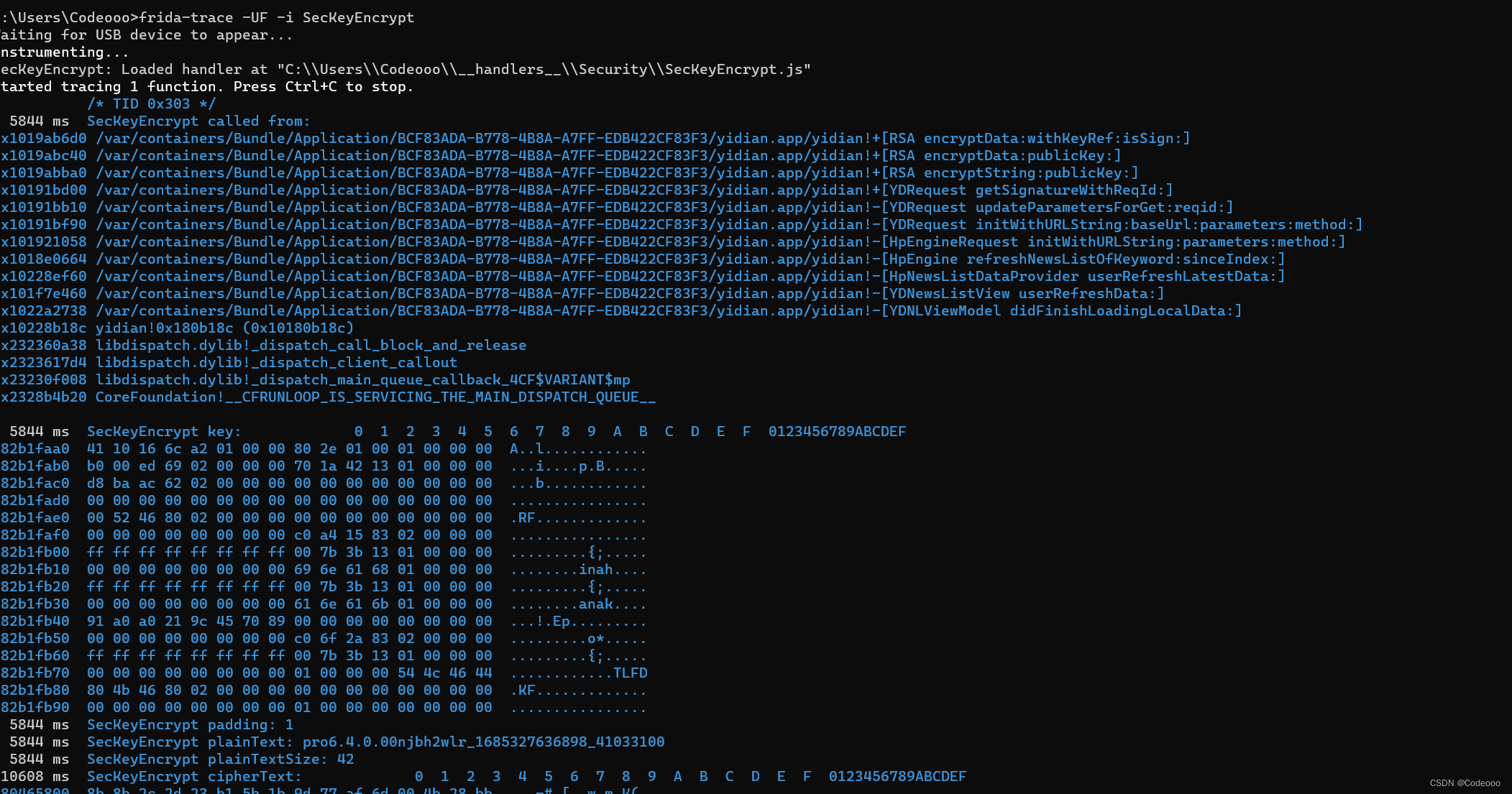
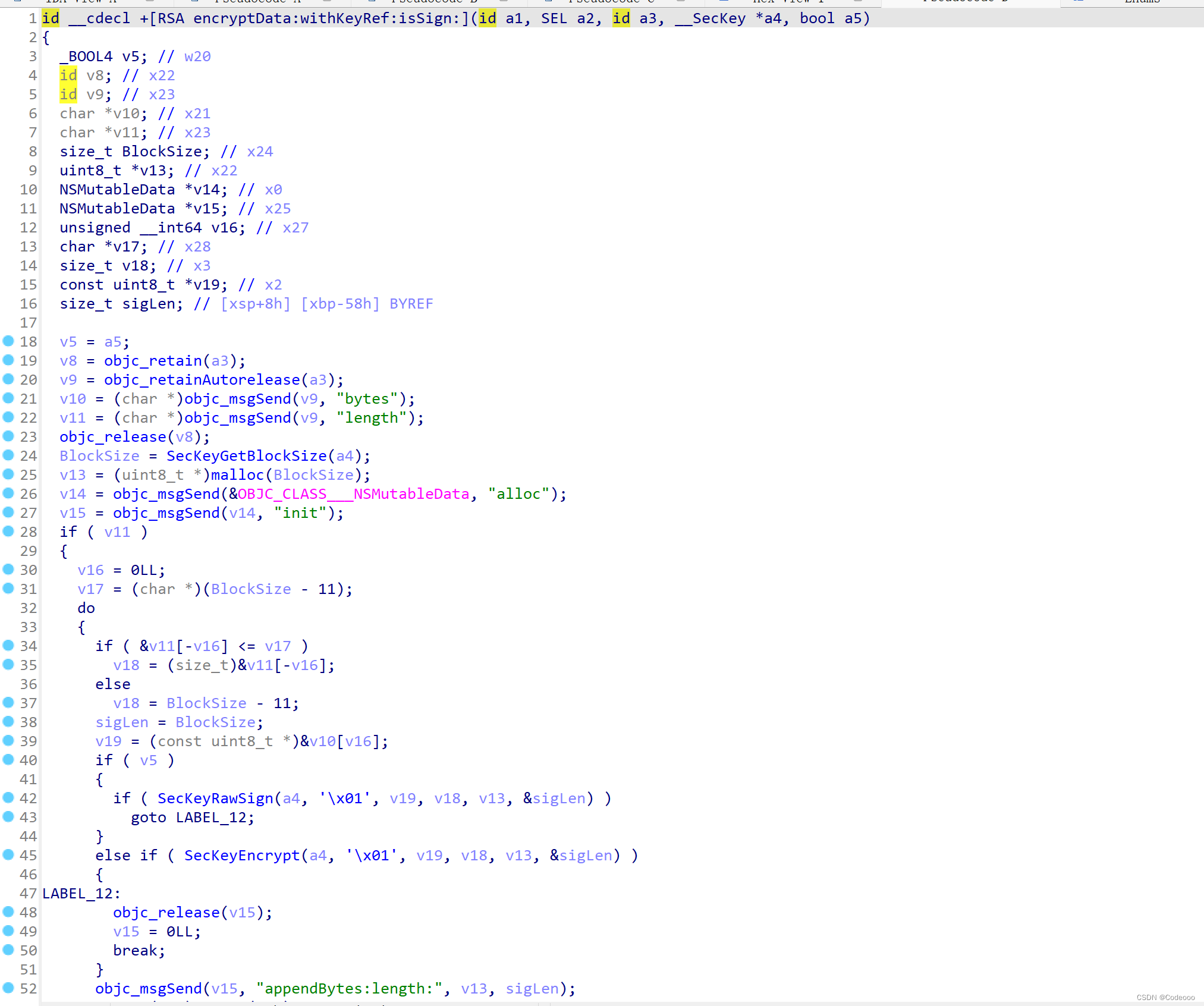
我们再hook下:encryptData:withKeyRef:isSign:
frida -UF -l hook.js 直接附加在该app上
var initWithMethod = ObjC.classes.RSA['+ encryptData:withKeyRef:isSign:'];
Interceptor.attach(initWithMethod.implementation, {
onEnter: function (args) {
// console.log('initWithMethod called from:\n' +
// Thread.backtrace(this.context, Backtracer.ACCURATE)
// .map(DebugSymbol.fromAddress).join('\n') + '\n');
console.log("args[2]: ", ObjC.Object(args[2]));
console.log("args[3]: ", hexdump(args[3]));
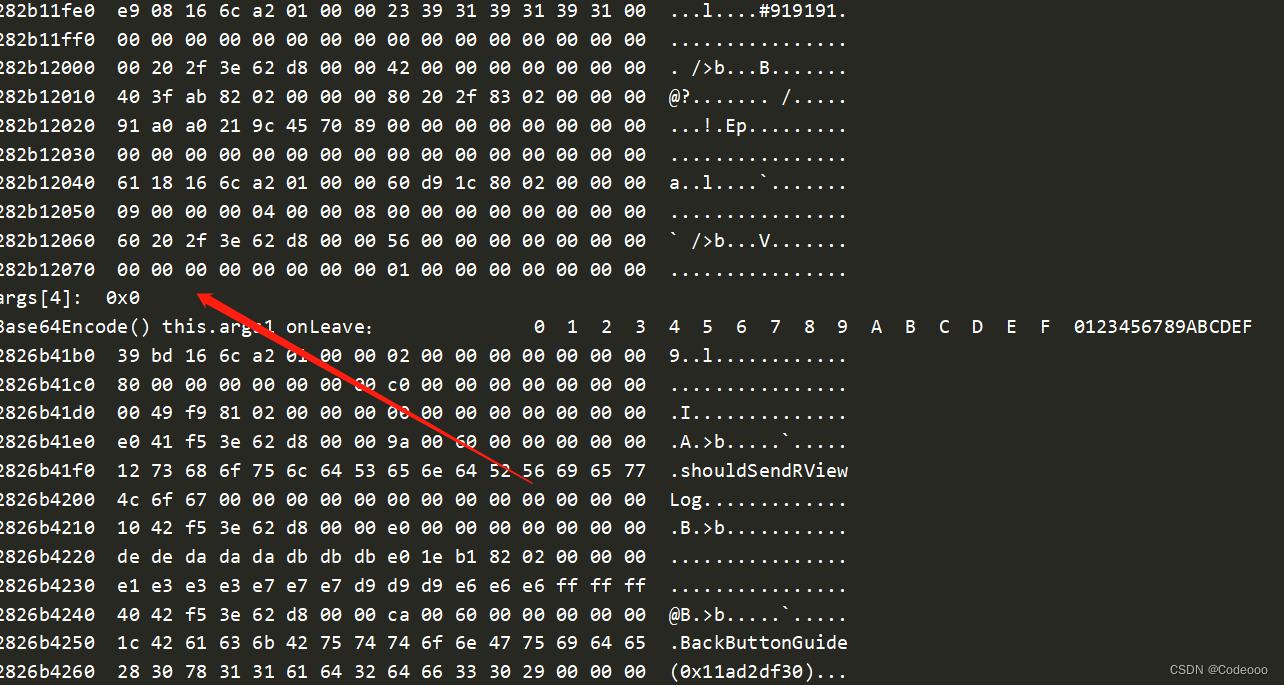
console.log("args[4]: ", args[4]);
}, onLeave: function (retval) {
console.log('Base64Encode() this.args1 onLeave:', hexdump(retval));
}
});
bool a5为 0,也就是false, 直接走
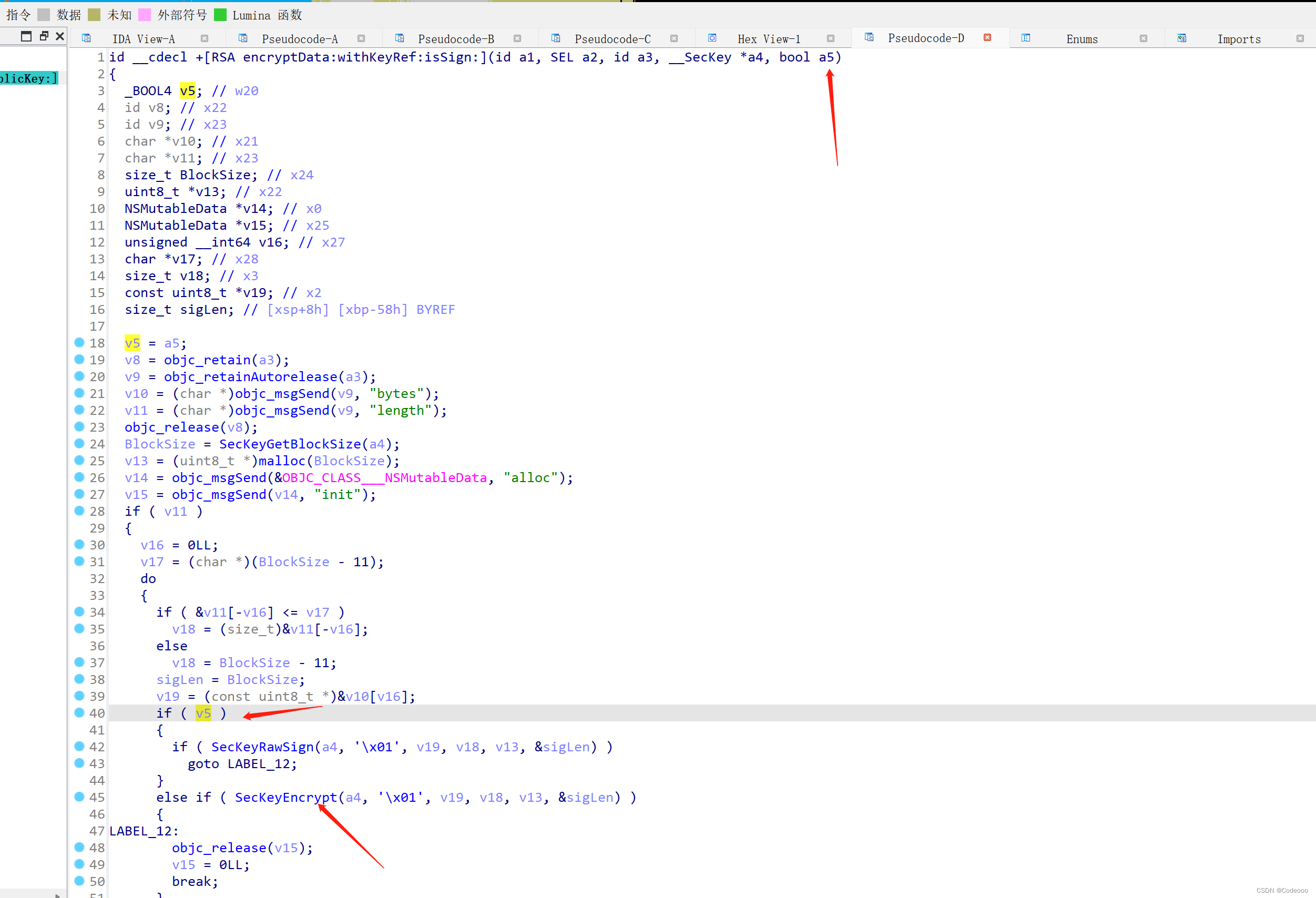
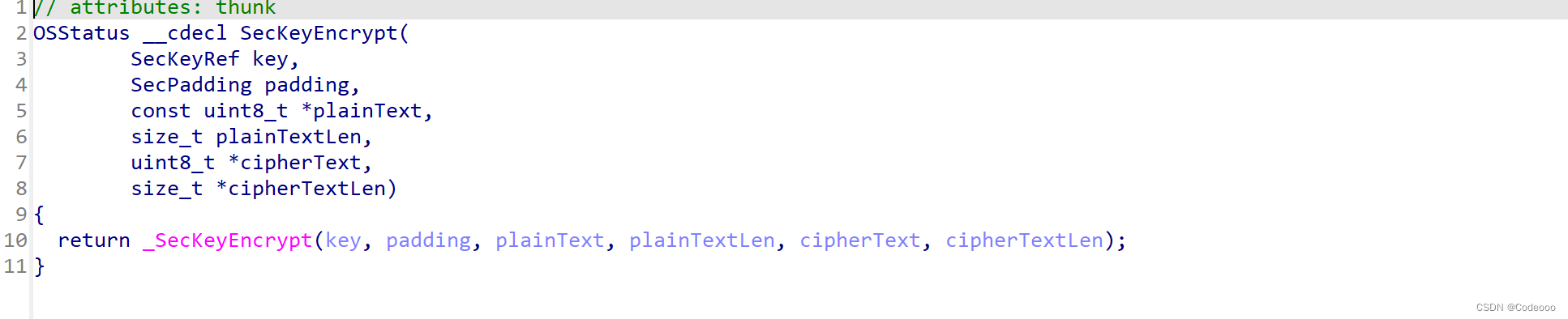
这个时候就明白了吧,这个地方就是上面的 最开始trace下堆栈及加密的地方了。
根据堆栈再往上看下吧:
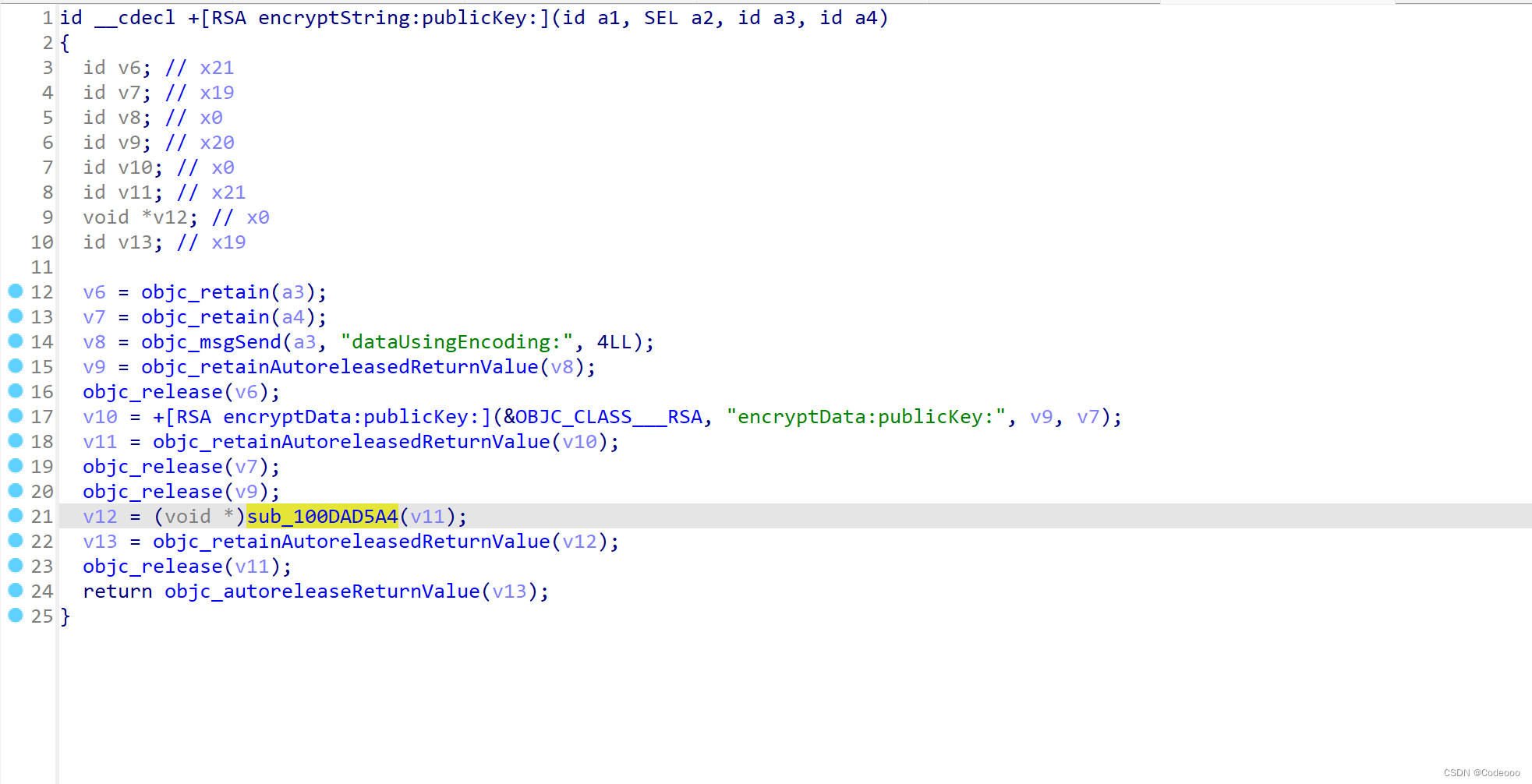
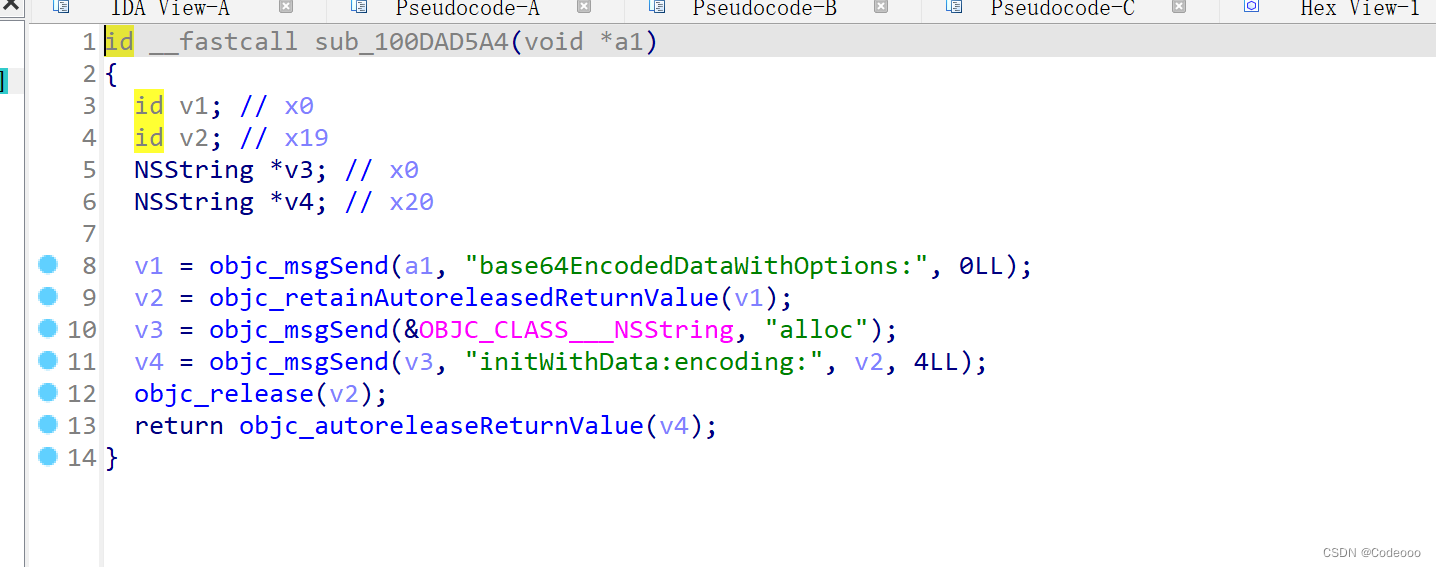
看到这里也是做了rsa然后base64, 没有其他操作
我们hook下吧:
var initWithMethod = ObjC.classes.RSA['+ encryptString:publicKey:'];
Interceptor.attach(initWithMethod.implementation, {
onEnter: function (args) {
// console.log('initWithMethod called from:\n' +
// Thread.backtrace(this.context, Backtracer.ACCURATE)
// .map(DebugSymbol.fromAddress).join('\n') + '\n');
console.log("args[2]: ", ObjC.Object(args[2]));
console.log("args[3]: ", ObjC.Object(args[3]));
console.log("args[4]: ",hexdump(args[4]));
}, onLeave: function (retval) {
console.log('Base64Encode() this.args1 onLeave:', ObjC.Object(retval));
}
});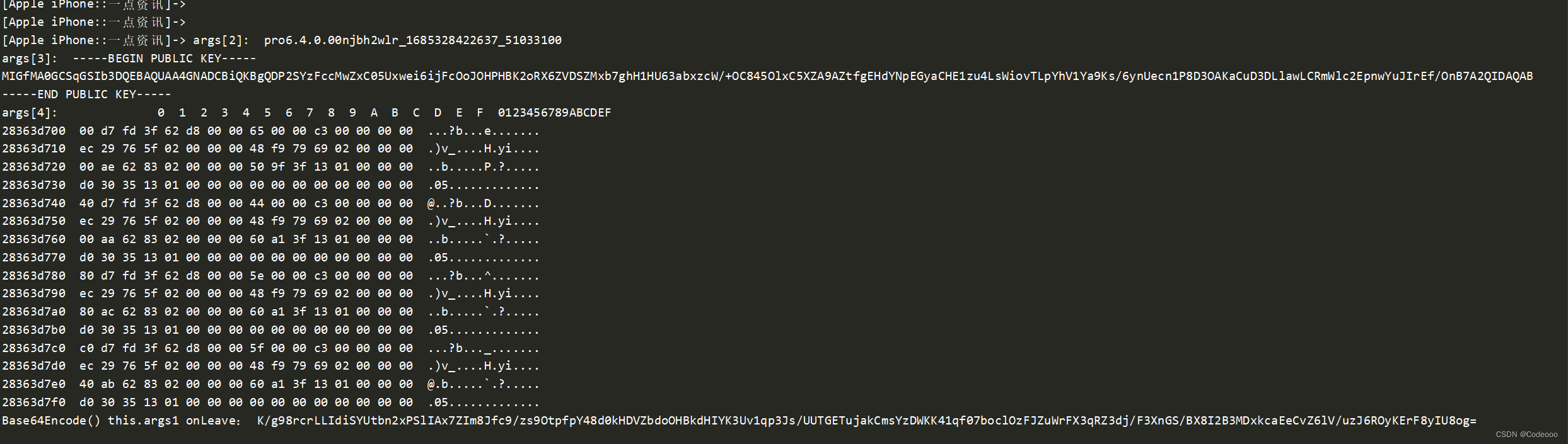
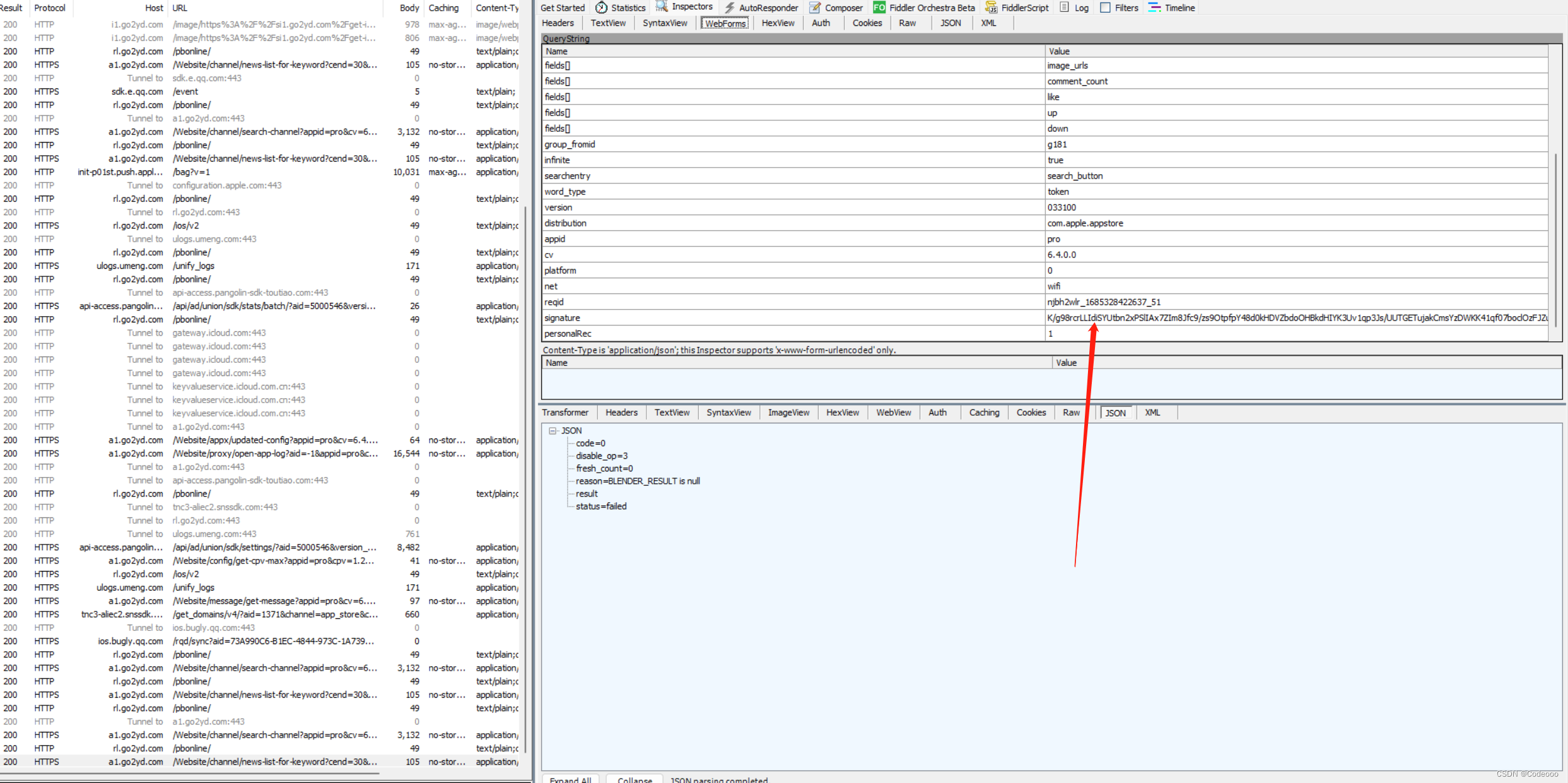
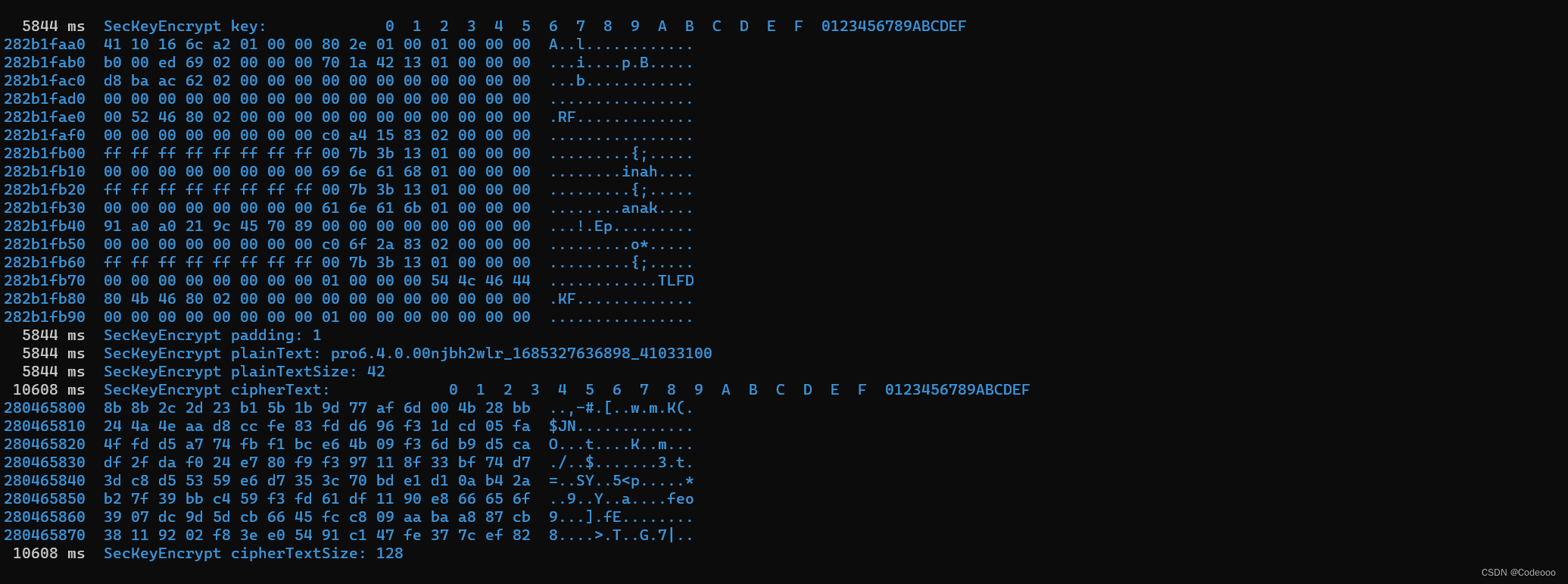
我去,这不就直接出来了吗
需要加密的值 :“pro6.4.0.00njbh2wlr_1685327378963_38033100”
入参拼接 appid、cv、platform、reqid、version
秘钥公钥也出来了。
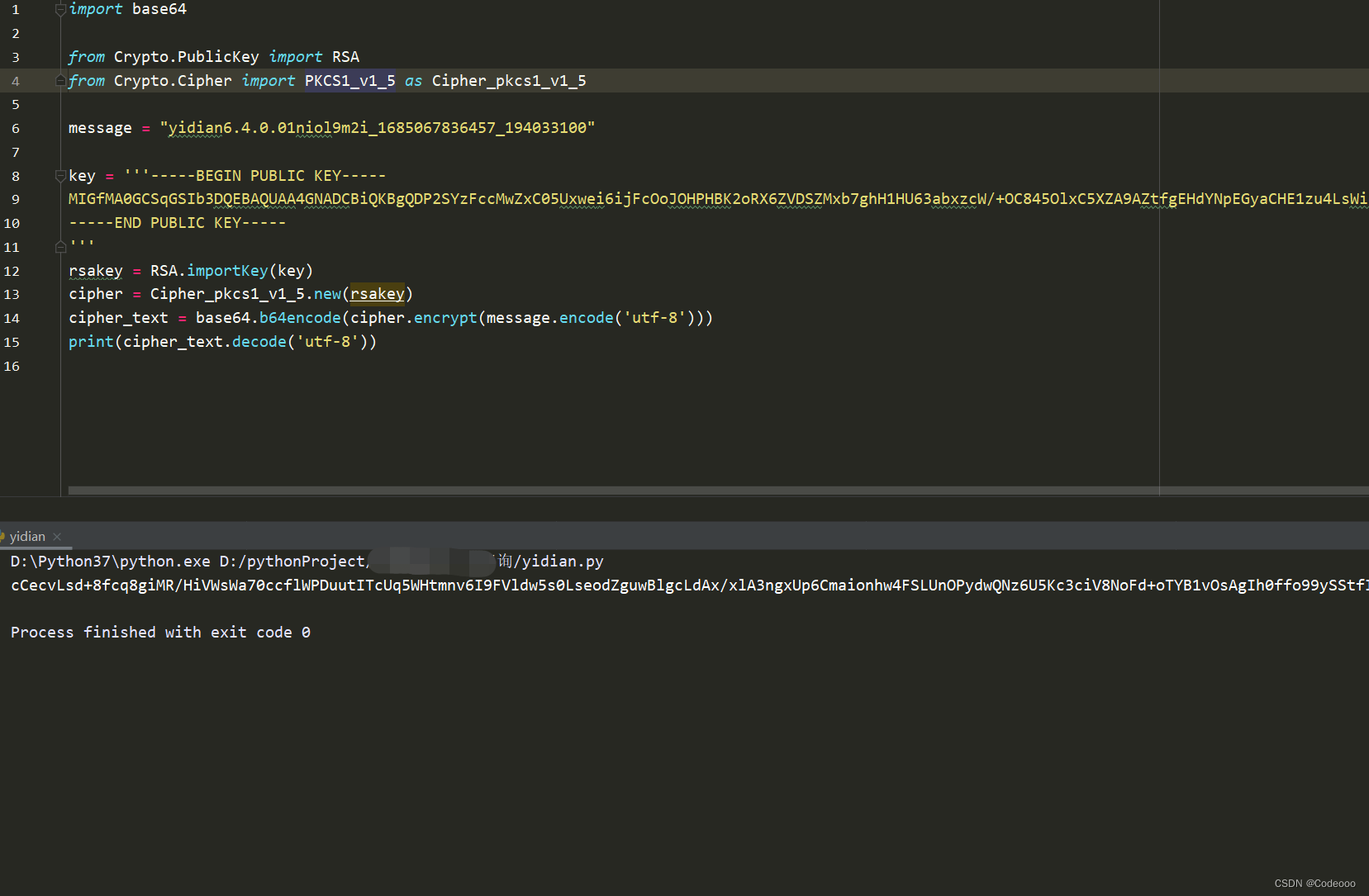
没毛病,收工!
68747470733a2f2f626c6f672e:6373646e2e6e65742f77656978696e5f33383932373532322f:61727469636c652f64657461696c732f313330393433353639